During a recent research into prevalence of open redirection vulnerabilities within the ccTLD .CZ we’ve done with my colleagues from ALEF CSIRT (description of its results in Czech may be foud here), I’ve noticed that many of the vulnerable sites seemed to be using CMS Made Simple with Babel multi-language module. This seemed to warrant a closer investigation…
Before we go further, let’s briefly describe what „open redirection“ (CWE-601) weakness/vulnerability actually is. The term is usually used to describe a mechanism which – when present on a certain website and queried in a specific way (usually by passing a specific parameter to it) - automatically redirects visiting browser to a different (arbitrary) domain/URL. What this means in practical terms is that it is possible to create a link to the website in question, which redirects user to any other - pontentially malicious or untrusted - site.
This behaviour might be intentionally present on certain websites, but in most cases, it is considered a vulnerability and/or bad practice since may be quite easily misused. Imagine, for example, how easy it would be to create a successful phishing campaign targeting clients of a bank which has open redirection vulnerability on its website.
An example of a site with intentional open redirection functionality, which will enable us to demonstrate the principle in practice, is 1gr.cz – a logger which counts clickthroughs for ad and marketing purposes. A link to 1gr.cz which automatically redirects visitors to untrustednetwork.net could be crafted in the following way:
http://1gr.cz/log/redir.aspx?url=https://www.untrustednetwork.net/
Now, let us dive right into the interesting details regarding CMS Made Simple and Bable.
CMS Made Simple (CMSMS) is one of the lesser known CMS platforms out there. Although it is not too widely used, vulnerabilities in the CMSMS core or in its plugins or modules may still affect thousands of websites. This appears to be the case with the vulnerability I found in Babel – a module which brings multilingual functionality to CMSMS sites.
The full write up of the vulnerability may be found here, but in simple terms, Babel in all its versions translates content by redirecting user to different pages based on their language preferences. This is not a bad idea per se, however in Babel, the same mechanism enables anyone to create a link to the CMSMS-enabled site, which redirects to an arbitrary URL.
Babel – when installed – uses the path domain.root/modules/babel to hold all its PHP files. Among these is redirect.php, a file containing PHP script through which the translation is handled. The relevant code looks like this:
|
|
What it basically means is that if the “newurl” parameter is set, browser will be redirected to the URL contained therein. Since there are no checks or limits regarding the target URL, the fact that there is an “open” redirection vulnerability should be obvious.
So how big of a problem is this vulnerability? Well, not too big. As has been said before, open redirection is mainly useful for phishing and not that many sites interesting to phishers use the Babel module… But with approximately 3.700 URLs affected before the disclosure was published it is not insignificant either. That number is based on relevant Google search results (so take it with a grain of salt - in terms of affected sites, it was probably a lot less…although the latest version of the vulnerable module was downloaded from the CMS website more than 5.700 times, so who knows) from February 14th 2019.
I was interested in the distribution of vulnerable sites/URLs around different TLDs, so I’ve done a search for each of the 20 most used TLDs and a serach for each of the ccTLDs of European countries. The “Top 10” results are:
| TLD | Count |
|---|---|
| ======== | ======== |
| COM | 1590 |
| BE | 448 |
| FR | 408 |
| NL | 227 |
| PT | 226 |
| CH | 207 |
| DE | 142 |
| CZ | 96 |
| LV | 78 |
| AT | 46 |
That covers most of what seems to be out there, but if you want to see the results for all top level domains with at least one relevant search result, they are summarized in the following chart.
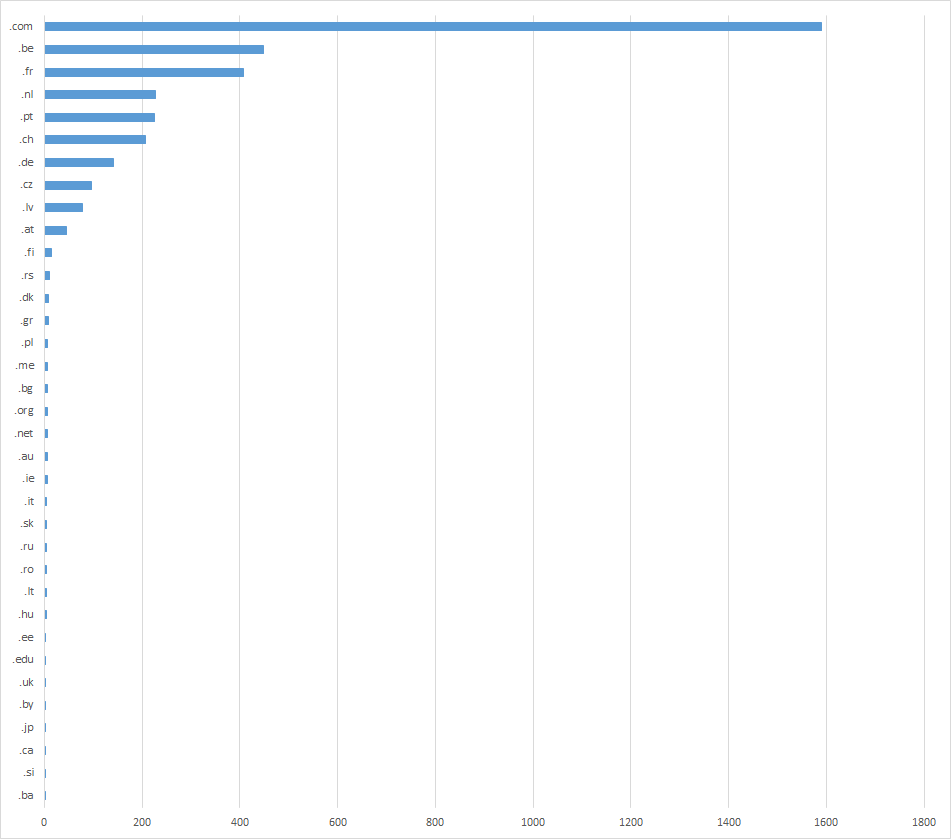
As you may see, a number of the vulnerable websites are hosted on domains within ccTLDs belonging to different European countries. What’s more, based on a quick look at the .COM results, it seems that most of those domains are also registered by European citizens and companies. I’m not sure whether CMSMS as a whole or just Babel have mostly Euro-centric user base, but this regional disparity seemes quite interesting either way.