TriOp update - version 1.1
· ☕ 2 min read
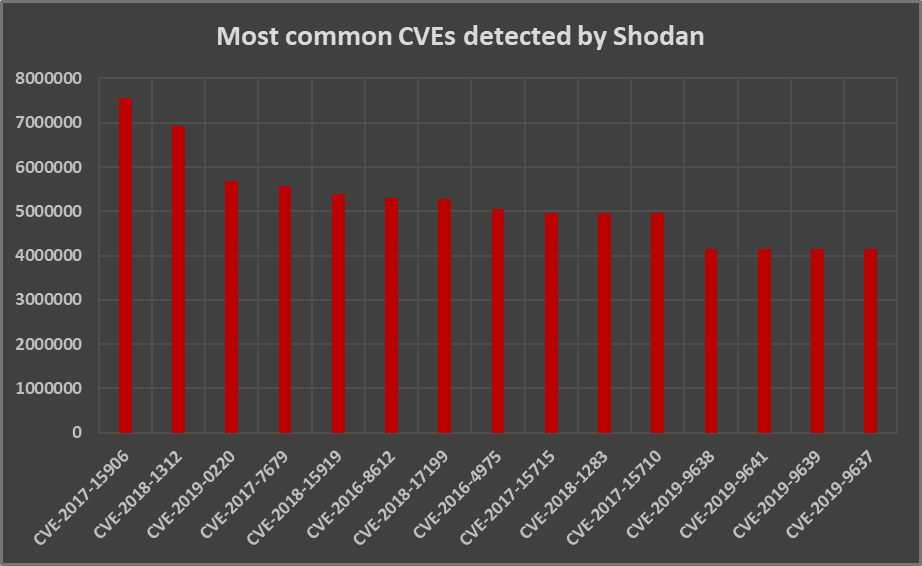
I’ve published version 1.1 of TriOp today. I’ve added CVEs for the recent Exchange vulnerabilities to the vulnerability search list, since Shodan is now capable of detecting systems affected by them. In response to a request from the CSIRT community, I’ve also added the option for use of arbitrary filter along with a list of parameters...