TriOp update - version 1.5
· ☕ 1 min read
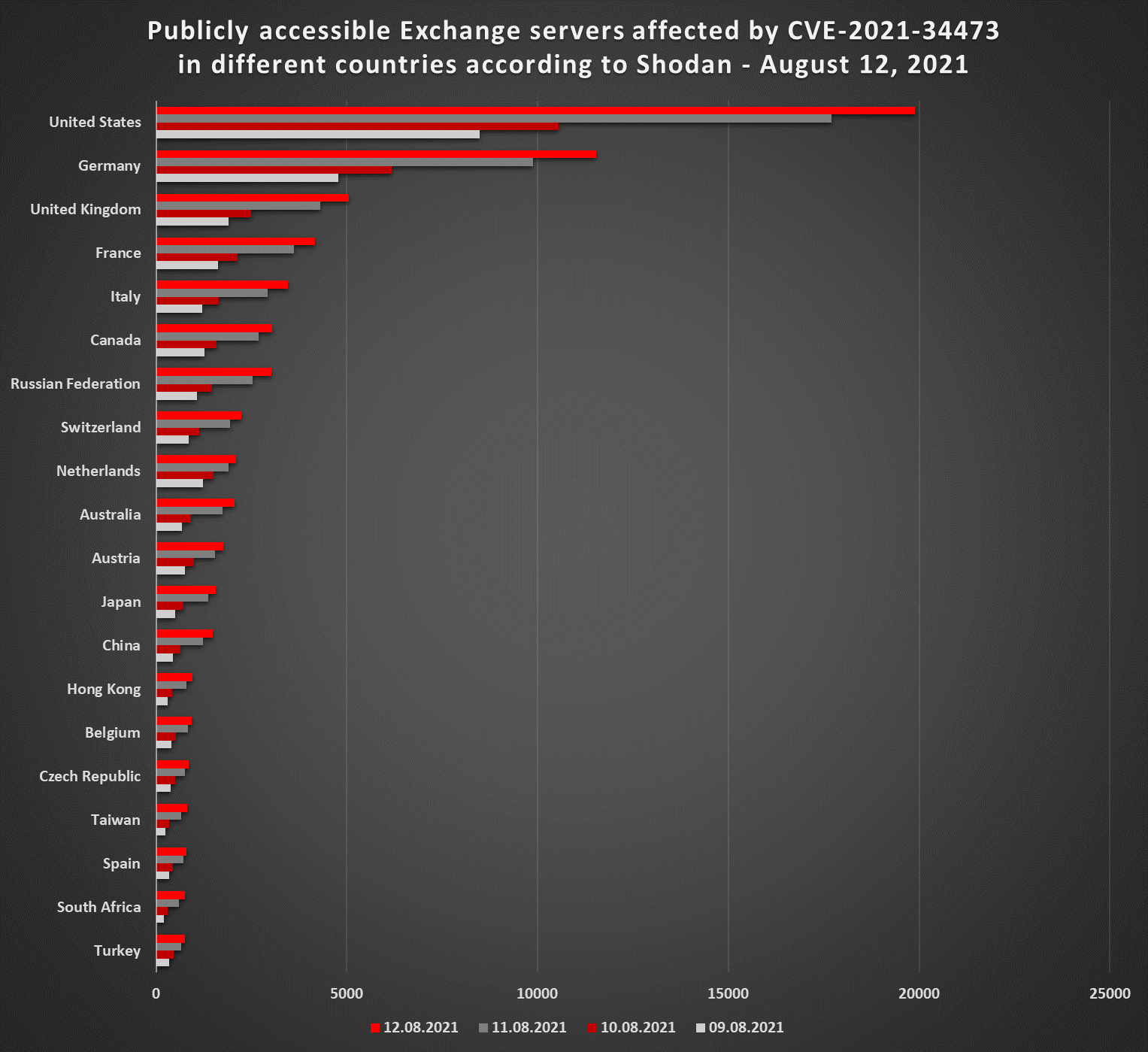
I’ve published version 1.5 of TriOp today. Besides the addition of several CVEs into the internal list of vulnerabilities, a new feature was also introduced, which enables automatic generation of Shodan queries for the current list of vulnerabilities from the CISA Known Exploited Vulnerabilities (KEV) Catalog...